Home > 8 business drivers to implement External Attack Surface Management (EASM)

1. Asset discovery & inventory
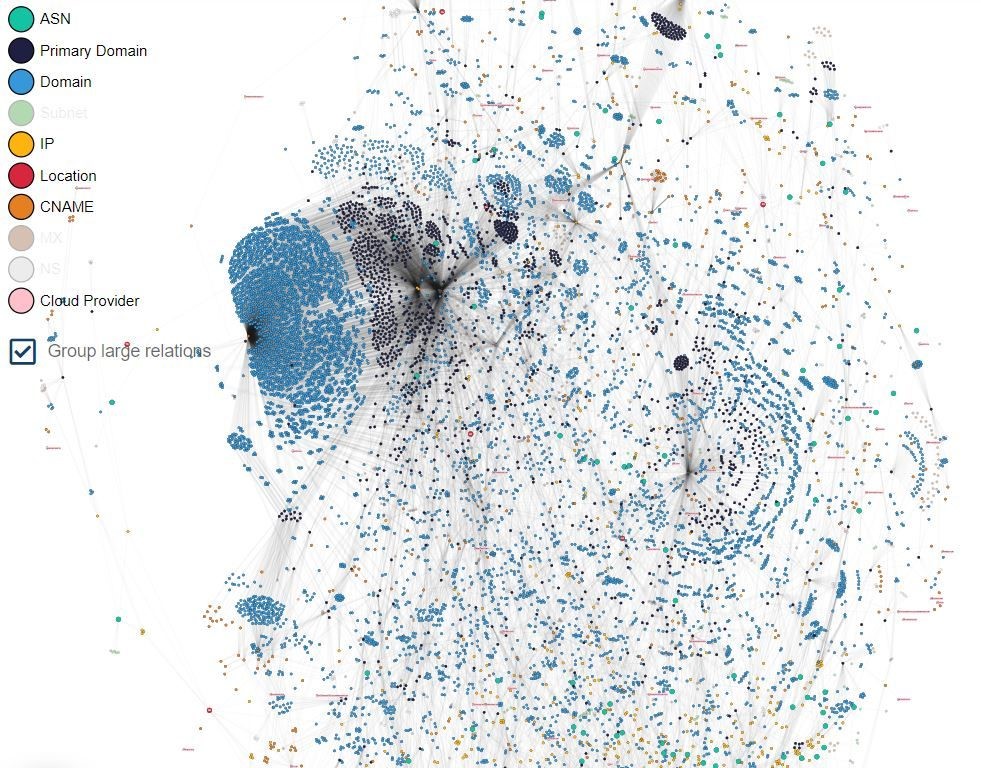
One of the prime values of External Attack Surface Management is the automatic discovery and inventory of all your company’s online assets. Running continuously, an EASM solution will keep a record of the known, unknown and unmanaged IT assets out there. The central internet-facing assets inventory that is built up, will automatically stay up to date. It will give you a real-time status of the external attack surface and warn you when new assets and issues arise. What you know, you can protect.
[Read more]
2. Attack surface scoring & reporting
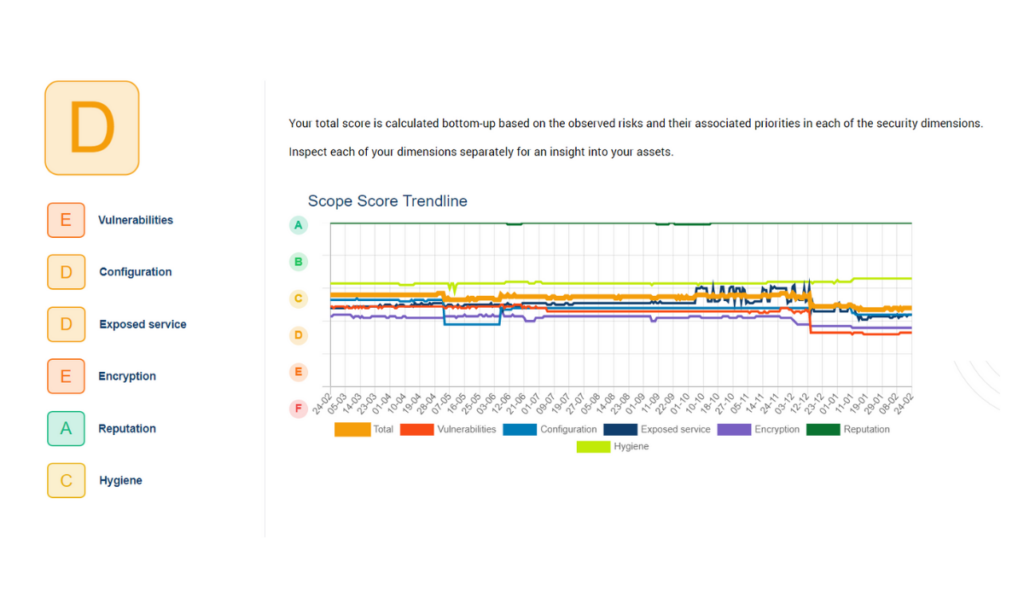
EASM solutions often offer an attack surface score. This is a rating of the company’s cybersecurity posture, indicating how well the attack surface is managed at a certain point in time and how it improves going forward.
The Sweepatic Platform rates the attack surface across the entire scope, on asset level and on observations (attack surface issues). For this scoring, 6 cybersecurity dimensions are taken into account, namely vulnerabilities, configuration, exposed services, encryption, reputation, and hygiene.
Next to the attack surface score, companies use the visual representations, trendlines and analysis in the dashboard in their reporting. Additionally, splitting the findings in the platform up in different subscopes for each of your brands or subdivisions, provides a specific report for every part of the organization.
[Read more]
3. Brand protection
In proactive cybersecurity solutions, brand protection is of course key!
Automated cybersquatting or look-a-like domain detection, including suspiciousness indicators, provide an early-warning system that can fuel your actions before a bad actor takes advantage. You can monitor possible phishing domains and make sure all your owned domains are in scope and continuously monitored.
[Read more]
4. Encryption certificate monitoring
With an EASM tool, you can keep an eye on your encryption 24/7. This is important, as proper encryption prevents data leakage and man-in-the-middle attacks.
[Read more]
5. GDPR compliance
A fifth business use case for EASM, is compliancy with the General Data Protection Regulation. In our Sweepatic Platform, this translates to knowing where all your internet-facing assets are physically residing in the world (and finding outliers in countries you have no relation with). Additionally, the platform tracks cookie consent violations on your websites. With these features, EASM can help to avoid a GDPR fine.
[Read more]
6. Mergers & acquisitions
EASM not only gets you automatic visibility on your own organization’s external attack surface, but also that of (to be) acquired companies. Needing minimal input and time, the Sweepatic Platform can provide an overview of the IT assets and issues fast – before or after mergers and acquisitions take place.
[Read more]
7. Shadow IT
Leveraging continuous internet-facing assets discovery, EASM finds unknown and unmanaged IT assets. This includes Shadow IT, which you will be made aware of so you can take the appropriate actions.
Furthermore, notifications will keep you up to date about new assets popping up in your attack surface. That way, you are always informed when a possible Shadow IT asset was about to be created.
[Read more]
8. Vulnerabilities & misconfigurations assessment
With External Attack Surface Management implemented at your organization, all the online assets discovered will also be analyzed for vulnerabilities and misconfigurations. The solution alerts you of any issues that you (urgently) need to review. This allows organizations to manage their attack surface accordingly and start the remediation process. Some examples include: exposed services, CVEs, SSL certificate problems, cookie consent violations and reputation checks.
[Read more]
Want to know more?
Sweepatic is specialized in External Attack Surface Management. Our cloud-native platform will get your organization up and running with EASM in no time.
So curious to see what your external attack surface looks like? Book a personalized demo and follow us on LinkedIn and Twitter to stay in the loop.