Home > The importance of cloud provider awareness

We at Sweepatic are continuously engineering new use cases to deliver footprint analysis and attack surface awareness by leveraging the rich datasets our very own Sweepatic reconnaissance platform is producing. Input and feedback from our customers and partners are crucial in this process just as our daily research on the topic is.
Since our use case library is growing, we would like to introduce our audience to some of these use cases.
Sweepatic use cases are delivered to our users in various ways, including machine readable exports, API access, a portal and/or intelligence reports:
Use case : Cloud Providers
Let’s start with the Sweepatic intelligence report on infrastructure awareness, and more specifically on discovering and analyzing cloud providers.
Its objective
After producing and analyzing the dataset of the customer, the report provides more context and insights to you on where all your servers are residing on the internet. Your organization has probably configured third party resources and seen the market trend (to expand via the cloud), your company has very likely been configured with different cloud providers too.
But do you know all these different, specific configurations for each cloud asset e.g. IP addresses, DNS, geolocation, cloud owners and their associated ASN (Autonomous System Number)?
Furthermore, this awareness oriented report provides a very detailed view on the current organization’s infrastructure and how its deployed, where the main part is located and how isolated and dispersed it actually is.
With the rapid pace of the internet and faster adoption of cloud in general, it is very common to lose track of all your internet facing assets and how these assets evolve over time, including assets tied to cloud providers. This report gives you visibility and tactical information, allowing you to be informed and take proactive measures ahead of something or somebody else. Details in the intelligence report include amongst others for the different cloud assets:
- Structure of the IP addresses
- IP owners
- Geolocation of the providers
- ASN informations
- Relationship graph of the different cloud providers
- Core versus isolated occurrences
Ultimately providing intelligence on your known and unknown exposed servers and applications and dispersed, isolated infrastructures.
Leveraging the Sweepatic capability
In a nutshell, it all starts with the large scale data collection in the Sweepatic reconnaissance platform of a defined scope(s). Our cloud based capability discovers and analyzes all exposed assets in your attack surface and builds and maintains an accurate asset register, accessible through a central and secure portal. The second step is the enrichment of the data, whereby annotations and tags are applied via both machine learning and via internal super tools leveraged by our own hunting activities.
Sweepatic hunters infuse a lot of OSINT techniques to gather additional public accessible related information. This information is then further processed, analyzed and shaped in an easy to read and understand Sweepatic report.
To gather this information, specific Sweepatic platform modules query DNS servers, search engines, regional internet registries and the customer websites.
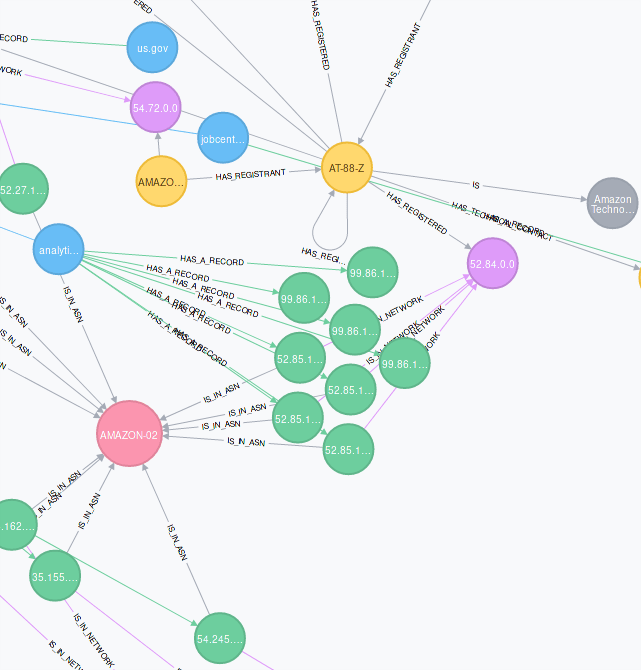
The information is then projected by our hunters into Neo4J, a graph database that allows quick vizualization and extraction of relationship patterns from the datasets at hand.
This relationship analysis allows us to conduct on demand and fast data analytics leading to the understanding of where all your servers are located on the web.
Having access to this kind of intelligence allows operational SOC and CERT teams to have an outside verification and control activity that provides them with access to actional information when they need it.
An example of the relationship graph used by the Sweepatic hunters is included with every Cloud Providers report as shown below:
Why is it important?
Organizations use the cloud more frequently than before – more than 70% of global companies according to Cloud Security Alliance. This makes their systems and data increasingly prone to attacks from the outside. According to the latest Verizon 2019 Data Breach Investigations Report:
- 69% of data breaches is performed by outsiders.
- Phishing and credential theft associated with cloud based email accounts have risen as a very prominent attack type.
- Over one-half of breaches via web applications attacks are associated with unauthorized access of cloud-based email servers.
The biggest difference with traditional security is that in the cloud every server is shared and reachable. The organization relies on a third party for their system and data storage. So cloud security has its own challenges, but that would lead us to far in this blogpost. Lets agree that it’s a shared responsibility between the organization and its cloud providers!
Contact us
So if we sparked your interest and you would like more information about our cloud provider use case, don’t hesitate and reach out to us via info(at)sweepatic.com or ping us via our social media channels.
We will introduce one of our next Sweepatic use cases shortly, so stay tuned!