Home > Do you know your attack surface?

By now, the term digital footprint shouldn’t be a mystery anymore. We roll our eyes every time we see an old college colleague, our teenage niece or that guy on Facebook we don’t really know exposing half of their life online. “Are they not thinking about the dangers?” we think.
On top of that, the term “digital footprint” covers the total web presence – uploaded elements plus data from analytic technologies, i.e. things beyond our direct control. So given that “every day, whether we want to or not, most of us contribute to a growing public portrait of who we are online” (Internet Society), how should we keep an overview of what can be found of us, if we don’t update a spreadsheet every time we surf?
Same same for organizations
For everyone who agrees rolling their eyes for the above reasons, I’d like to propose an experiment.
Think about the company you work for. Does it have 10 or 100 or more internet domains under control? How big is its digital footprint? Internet domains spanning each 50 active subdomains? Or 500? Which web applications and files are exposed? Do they leak sensitive information? How are new assets in your company reported to the risk & security stakeholders? Is there an inventory of all assets and is it complete and up-to-date?
"Good questions… difficult to answer… New assets have to be reported to someone who reports it to another one who will, after having it signed by different managers, put it in a spreadsheet.”
If that’s somehow close to what you were thinking then don’t worry, we observe this in 95% of our customer meetings. You’re not alone. “Risk, Security and IT teams are having difficulties to cope with all the work and their visibility of what they have to secure (availability, confidentiality and integrity) is fading with the increasing complexity and dynamic nature of digital footprints.” (Stijn Vande Casteele, Sweepatic CEO).
Now, it’s hackers rolling their eyes with a grin on their face: “They’re not aware of how much valuable intel I’ll find in their mess! :D”
Anyways, we believe, in order to gain visibility and spend money adequately, the question is not if wether or not an organization is aware of the dangers, but if it has the capability to keep an overview and spot weaknesses (before they become dangerous) in an ever growing attack surface that is the digital footprint.
Apropos Attack Surface.
I used “ever growing”, but “exponentially growing” would fit better.
"With Industry 4.0, “the convergence of cloud, mobile, social and data have ushered in a new wave of business models that will present unique challenges for various industries” said Bob Weiler in Forbes.
Especially IoT devices will drastically expand the attack surface of organizations (https://accenture.com) (oil and gas companies for example).
If an organization wants to remain competitive, this expansion through technology is inevitable and enables many new possibilities to threat actors. Actively taking control over the presented opportunities is therefore of utmost importance, for it will positively reflect on performance, risk, and financial management.
Actively take control.
Deloitte correctly points out: “While defenders are compelled to plug every security gap in their complex, changing environments, the attacker only needs to take one successful action to achieve their win.”
With all this in mind, it’s not too surprising that “90% of CIOs admit to wasting millions on inadequate cybersecurity” (https://venafi.com), because:
Time and productivity are lost through manual, slow and human processes, that are unreliable AND uncontrollable.
Even the best of the best cyber security capabilities, if fed with incomplete data, will produce unreliable intelligence.
The cost of inadequate decisions based on unreliable intel is huge.
Let a machine do it.
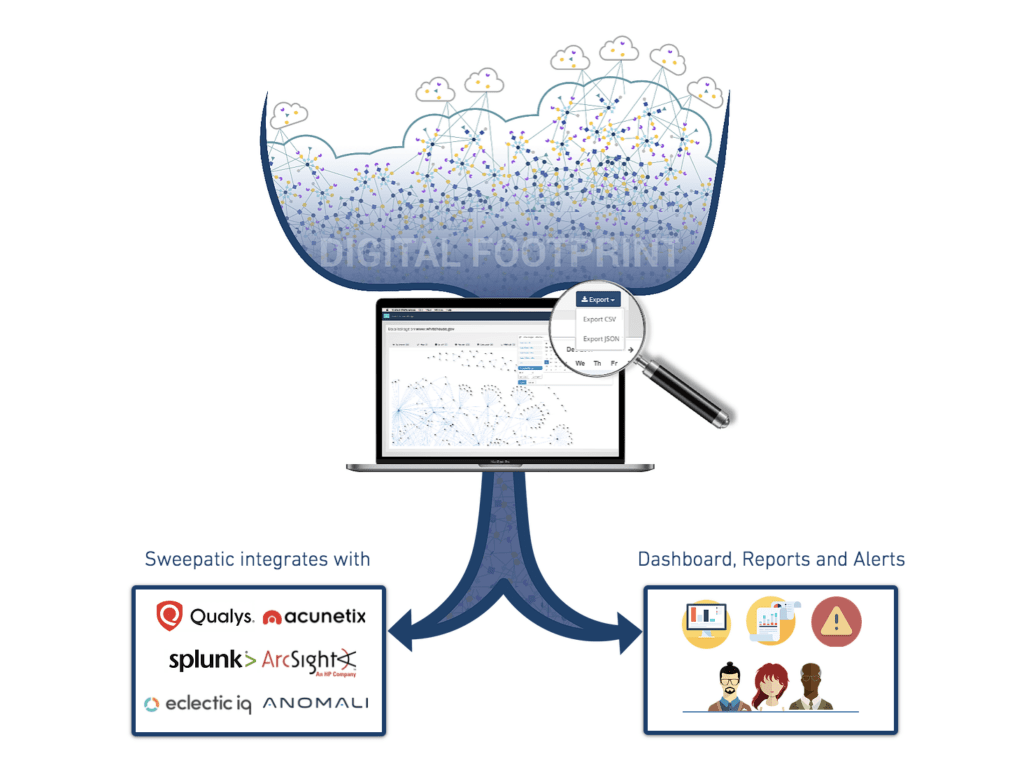
Our solution replaces this old process. With our top notch reconnaissance techniques, the Sweepatic solution discovers every little bit of your digital footprint, and explores every oh so hidden and forgotten place for weaknesses – no need for slow reporting processes or static inventory spreadsheets.
After a sweep by our solution, we’ll enrich you with actionable information in the form of:
- all your existing and active subdomains.
- which subdomains are vulnerable to subdomain takeovers.
- what web applications/technologies/files each of them contains.
- which information is exposed and where (WHOIS, DNS records, PII, used software, file paths…)
- all potential cybersquatting domains out there.
- and much more!
For more information and a free preview, visit our website or directly contact us via info[at]sweepatic.com.