Home > Dive into reconnaissance and MITRE’s PRE-ATT&CK

In this blogpost, we will explain the preparation phase of threat actors. We will explore reconnaissance – the playing field of the Sweepatic Reconnaissance Platform, of course – and dive into the MITRE (PRE-)ATT&CK framework.
The Cyber Kill Chain
Cybersecurity has come a long way from the nineties hackers spoofing IP addresses to bypassing firewalls, to advanced persistent threats capable of breaching critical information infrastructures. Script kiddies working 9-to-5 and “hacks and phreaks” transformed into well-defined tactics and procedures. It became a business. For some the cyberspace has been officially declared a war-space, and so the cyber-warfare has evolved into a military domain.
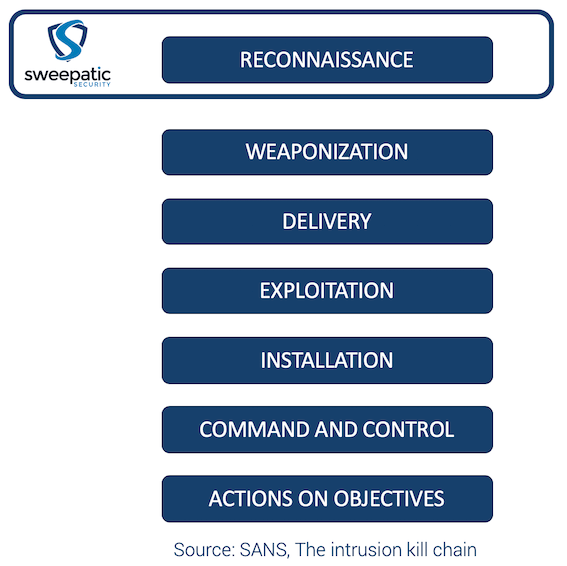
It is actually from the military space that the term “kill chain” comes from. The Cyber Kill Chain defines the structure and stages of an attack. Lockheed Martin was the first company to adapt it to the cyber space by creating a set of 7 phases. Below you can see the version SANS made.
Widely adopted by the industry but criticized for its malware-centric and perimeter focused approach, this kill chain has been the main starting point to better understand the tactics and procedures of common threats until recently.
The ATT&CK framework
In order to provide a more precise and granular standard, MITRE defined the ATT&CK framework. The ATT&CK framework is a matrix containing all the potential techniques, tactics and procedures (TTPs) of an attacker, allowing an easy description of a specific threat actor by overlapping or linking TTPs together.
ATT&CK is becoming the industry standard to understand threat actors capabilities and specificities. The focus on practical attacks by the framework is appreciated because it allows the defenders or blue teams to mitigate and setup defenses against specific techniques.
The PRE-ATT&CK framework
For an attack to be successful, the threat actor has to acquire a precise knowledge about the victim organization and infrastructure.
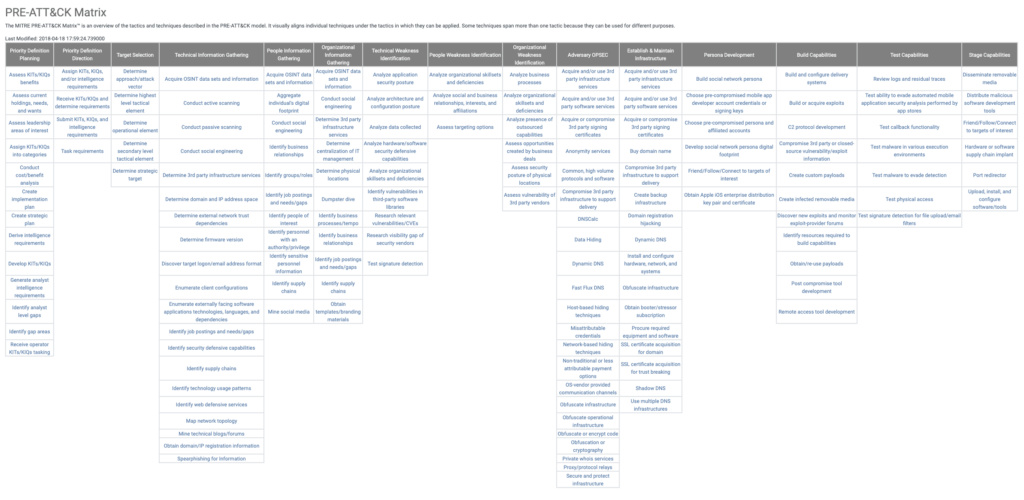
This operation preparation includes target selection, reconnaissance, weakness identification, operational security and operation installation. Those steps are precisely described in the ATT&CK framework cousin: PRE-ATT&CK.
PRE-ATT&CK is the non-intrusive and intelligence-based counterpart to ATT&CK, created to describe better the techniques, tactics and procedures of an attack preparation.
PRE-ATT&CK is unique in the sense that it focuses on techniques that cannot be mitigated directly with network and system defenses but with organizational processes and trainings. PRE-ATT&CK is a newcomer and covers the missing part of the warfare: the intelligence gathering.
Its goal is to make fellow organizations less attractive for an attacker, understanding which threat actors can target an organization and how to prioritize cyber threat intelligence data acquisitions to detect early weak signals of an incoming attack.
The PRE-ATT&CK Matrix: https://attack.mitre.org/matrices/pre/
Understanding the threat
PRE-ATT&CK focuses on 5 main aspects of the preparation:
- Priority definition and target selection
- Information gathering
- Weakness identification
- Operation installation
- Capabilities development
Understanding each of these aspects helps an organization to better assess who to defend against and how. Let’s see how.
Every attacker has a motive, a goal, an objective. They try to either steal sensitive information, or tamper with existing information or destroy systems.
Priority definition is the process of assessing what is the objective of an operation. What defines the success criterias, the requirements and the attributes of the targets. Understanding the methods and process helps drastically in filtering the threat actors into actual threats for an organization. Filtering threat actors allows a security team to prioritize and decrease the costs of the security requirements. An example of such an excercise for an industrial-espionnage focused APT, is to understand the area of interest (cybersecurity, defense industry, technology based companies or even scientific research centers) of the attacker, and to position the organization to seek a match.
Information gathering aggregates all the tactics and techniques for the attacker to better understand an organization as a target. If the attacker manages to know details that the victim misses, it increases the chances for an attack vector to be successful. The reason behind this statement is that for an organization to protect its assets, it has to manage a list to assess the potential attack channels, route and vulnerabilities. Information gathering is the definition of the map of an organization, an incomplete map from a defender perspective results in a potential backdoor. Subdomain enumeration and social networks analysis are two areas of information gathering.
Weakness identification focuses on the vulnerabilities side of the information gathering. A good patch management, employee training and security measure results necessarily from a weakness identification process. Offensive weakness identification can come from vulnerability scanning, social engineering bait testing or target profile psychological assessment.
Once the attacker gathered all of this, he will focus on the operation installation. This entails deploying offensive infrastructure, developping personas for social engineering purposes, using operational security (OPSEC) to protect its operation and acquiring equipments and software. It is very difficult for an organization to detect such preparation, but there are counter intelligence methods to do so. Open source intelligence (OSINT) can help detecting early newly-registered domain names which leverages the organization brand name in a malicious way. More on the cybersquatting (or domain squatting) topic in on of our upcoming blogposts.
Building the implant and developing capabilities that are specific to a target weaknesses and profile increases the success rate. It is nearly impossible to detect malware development and testing, but focusing on early weak signals of capability staging (counter intelligence protecting potential victims and areas of interest) can be prioritized only if we know the tactics and procedures of the threat actor. Detecting unusual behaviours through automated analysis or physical surveillance can bring an organization a step ahead of the attacker.
Threat Intelligence driven red teaming (aka TIBER)
PRE-ATT&CK is not a tool, nor a method. PRE-ATT&CK is a framework to have a better understanding. However, if an organization understands its threats, it can emulate it and train its heroes against specific tactics and techniques.
In Europe, a legal framework for financial institutions to organize security assessments has been created under the name TIBER-EU for Threat Intelligence Based Ethical Red teaming. This framework states that penetration testing has to be based on known TTPs from specific threat actors relevant to the financial institution. The assessment has to be made by two different teams: one team creates the threat intelligence (TI), the other one executes the attack scenario.
This European framework finds its own implementation in each country, for example TIBER-BE in Belgium, and builds on pre-existing national initiatives like TIBER-NL in the Netherlands and CBEST in the UK.
PRE-ATT&CK is a great framework to fit into TIBER-EU. It describes all the TTPs that can be followed by the TI team to create a realistic scenario and filter threats.
Conclusion
PRE-ATT&CK is an interesting newcomer that sets a new standard for offensive operations preparation. It fills an empty space in a security market to offer organizations a better understanding of the value of reconnaissance and intelligence gathering.
At ATT&CKcon, the MITRE ATT&CK conference, you can learn more about MITRE’s work in cyber threat intelligence and the frameworks. The conference takes place 28-30 October in Virginia and will be streamed live.
Closer to our Sweepatic HQ (for the European readers), the EU ATT&CK Community organizes a one day workshop during the Cybersecurity Week in Luxembourg taking place 15-25 October.
Sweepatic is looking forward to further collaborate with the community on the further developments around ATT&CK and more in particular the PRE-ATT&CK framework.
Until next time!