Home > What is the difference between an external attack surface management solution (EASM), a vulnerability scanner, and a pentest?
- Kris Jehaes
- Article
What is the difference between an external attack surface management solution (EASM), a vulnerability scanner, and a pentest?
Many people wonder how an external attack surface management (EASM) solution is different from a traditional vulnerability scanner or a penetration testing exercise.
These solutions partially overlap on some use cases, but in essence, they are not in competition with each other. In fact, they augment each other. The next question that is raised is: in which one should I invest first? There is no single right answer here, it all depends on what you want to achieve, and which tools you have today.
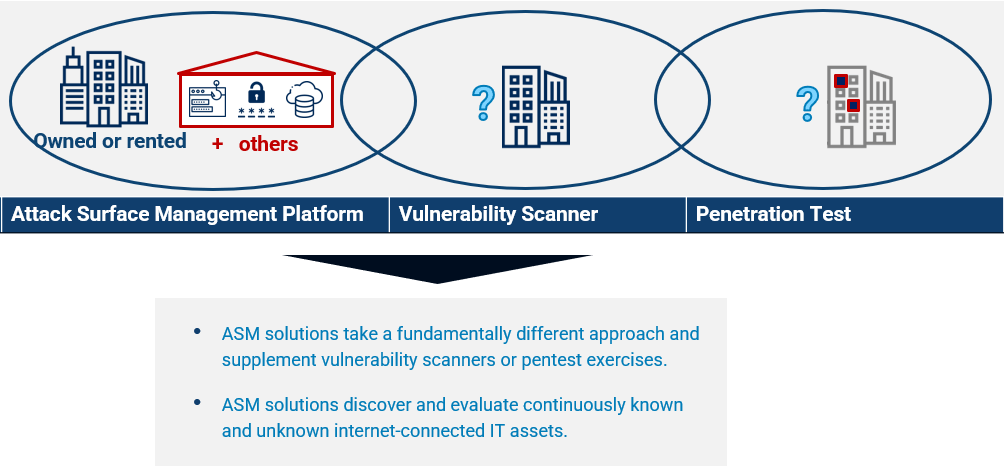
Let’s say the total external attack surface of a company is like a set of buildings it owns or rents. An EASM solution will try to find and inspect them all by walking around in the streets. A vulnerability scanner will only inspect the buildings that were specifically assigned to it using an address. The penetration test will try to break into one of those buildings by only looking at some windows. Additionally, the EASM solution might also inspect other buildings that are not owned or rented by the company to look for risks and threats for the company.
In this article we will further discuss the differences summarized in the following topics:
- Scan scope, required setup and input needs
- Scan aggressiveness, timing and approvals
- Presentation and follow-up of the results
- Additional differentiating features of EASM solutions
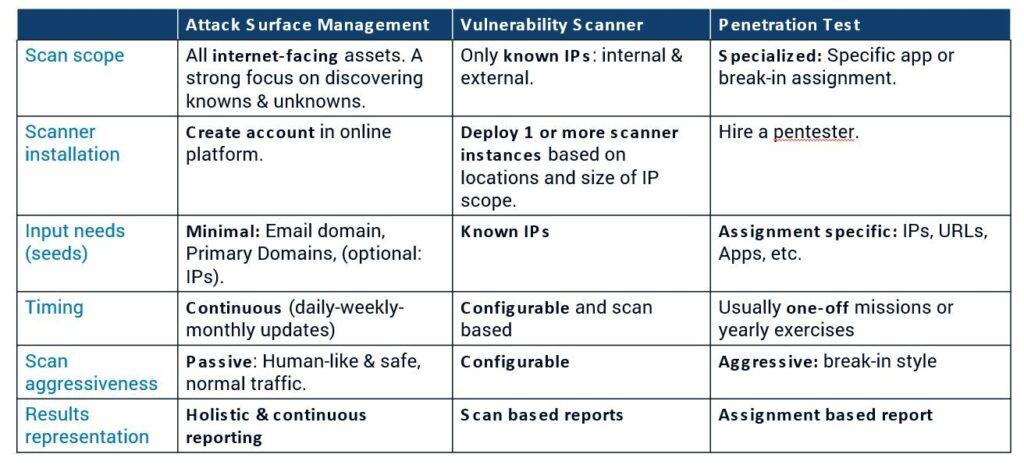
Scan scope, required setup and input needs
EASM solution: The primary goal of an EASM solution is to discover and analyze internet-facing IT assets and risks without needing much input or seed values. A company name or some primary DNS names should be enough. Based on limited information, its first goal is to make it easy to discover all internet-facing assets without knowing, where, how or by whom they are deployed.
EASM scanners specialize in the discovery of both known and unknown assets based on DNS information and not IP addresses. They don’t need a lot of input to get started. Without exception, these tools are easy to set up as they are offered as a SaaS cloud service and require minimal input.
Vulnerability scanner: The primary goal of a vulnerability scanner is to find software vulnerabilities based on a set of IP addresses that you need to provide. So by definition you will only be discovering IT assets within the known ranges of defined IP addresses.
With an IP based scanner you will never discover any unknowns outside of the defined IP ranges. With a vulnerability scanner you can decide to scan both internal and external IT assets, as long as the IP address can be reached by the scanner. Finding that list of IP addresses requires detailed technical knowledge. EASM solutions can augment vulnerability scanners by delivering the input for all public IP addresses, as this is part of their discovery work.
Penetration test: The primary goal of a penetration test is to break in. A penetration test usually has a very narrow scope and is set up in order to test a specific app or to discover and execute a break-in scenario.
A penetration test is usually assisted by an automated vulnerability scan and a external attack surface discovery tool in order to determine to best opens for breaking in. A penetration test almost always requires manual work done by security experts.
Each of these solution are specialized in different outcomes.
Scan aggressiveness, timing and approvals
For every scan solution it is important to know if it can break or crash an IT asset and how often the scans are conducted.
EASM solution: The conducted scans are safe by default. They are based on conducting normal network traffic towards infrastructure, services and apps in order to compile as many insights as possible from the responses.
The scans are automated, continuous and do not need to be scheduled or configured. Scans are iterative and learn from each other. The discovery of for instance a web server, can trigger a more specialized web scanner. The web scanner might discover other web servers, that will trigger additional web scans, and so forth. Due to the safe nature of EASM discoveries and scans, they are ideal for assessing the cyber security posture of partners, suppliers and others in an objective way.
Vulnerability scanner: Every scan needs to be planned and configured. The configuration needs to be done by experts based on input like IP addresses, scan aggressiveness, which tests to include or exclude. The scans can even go into a real attack mode depending on how aggressive the scan is executed. As such, it automates part of the manual work of a penetration tester. Care must be taken when using aggressive scans as they can damage systems or even bring them down.
Depending on the use case, scans might be repeated every week, month, quarter, year or ad hoc. Due to the inherent risks, vulnerability scan windows must be planned and approved.
Penetration test: The test is by default potentially dangerous, as a break-in might also break functionalities. Manual work and human intelligence is required as these test will go beyond what a vulnerability scanner can do automatically. Due to the inherent risks, penetration test are usually conducted on staging systems or just before going into production.
A penetration test is usually conducted as a one-off exercise, or at maximum repeated at a much slower pace, like once or twice per year, depending on available budgets, time and risks. Generic break-in scenarios are planned and conducted with the approval of higher management.
Presentation and follow-up of the results
Presentation and follow-up of the results are handled differently.
EASM solution: The results are continuously updated and represented per asset type, risk groups, etc… The risks are represented per asset and are not linked to specific scans. The focus is not only on alerting about vulnerabilities, but also on creating a complete asset inventory, and looking at other indicators that might flag IT assets for decommissioning or as shadow IT. An EASM solution can alert on vulnerabilities based on the version numbers that services leak from there network traffic. As such, they behave as a light and safe vulnerability scanner.
Vulnerability scanner: The results are typically presented per scan and focus on vulnerabilities that are related to a CVSS score. Other use cases like attack surface reduction are not so prominently tackled. It is not always easy to follow the risks and evolution trends of individual assets or asset groups over different scans.
Penetration test: The findings are usually represented in a human written report. This report is discussed and the relevant risks are solved by the technical staff. It is not usual that a second test is done to verify that the fixed issues are actually fixed.
Additional differentiating features of EASM solutions
Additionally to looking very broadly at finding all the IT assets a company uses, some EASM solutions also look at risks for the company from IT assets of external bad or accidental actors. These risks can be:
- Look-a-like websites that are abusing the brand.
- Insecure passwords because of stolen and leaked account details of employees or customers.
- Stolen credentials that are sold on the dark web or distributed elsewhere.
- Other sensitive data of the company or its employees that are leaking.
Sweepatic is an External Attack Surface Management Solution
Our customers leverage the Sweepatic Platform’s discovery capability to continuously find known and unknown IT assets. Additionally they use our platform to follow up on a prioritized list of security issues discovered.
On top of our powerful discovery engine, we automatically inspect and report on security issues like vulnerabilities, misconfigurations in email/DNS/Web, weak encryption, expired and weak SSL certificates, exposed databases and file shares, exposed administrative access and much more.
To schedule your personalized demo with one of our Sweepatic experts, click here. Feel free to subscribe to our newsletter to stay in the loop. We promise we won’t spam you.